The Creeper program, created in 1971 by Bob Thomas, is widely regarded as the first self-replicating program and an early example of a computer worm. It ran on ARPANET computers using the TENEX operating system. Creeper was not malicious, did not damage data, and spread by moving itself between.
Meta Title: The Creeper Program: The World’s First Computer Worm (1971)
Meta Description: Discover the history of the Creeper program, Bob Thomas’ 1971 experiment on ARPANET. Learn how this non-malicious, self-replicating pioneer shaped cybersecurity.
The Creeper Program: The First Computer Worm and Its Non-Malicious Legacy
In the early days of computer networking, an unassuming experiment paved the way for modern cybersecurity conversations. The Creeper program, developed in 1971 by Bob Thomas at BBN Technologies, holds the distinction of being the first self-replicating program and an early precursor to the computer worm. Designed not to harm but to demonstrate theoretical concepts, Creeper ran on ARPANET—the experimental network that laid the groundwork for today’s internet. Here’s why this digital artifact remains a cornerstone of tech history.
What Was the Creeper Program?
Unlike modern malware, Creeper was a non-malicious proof-of-concept created for the TENEX operating system. Its purpose was simple:
- Self-Replicate: Move autonomously between limited-memory ARPANET computers.
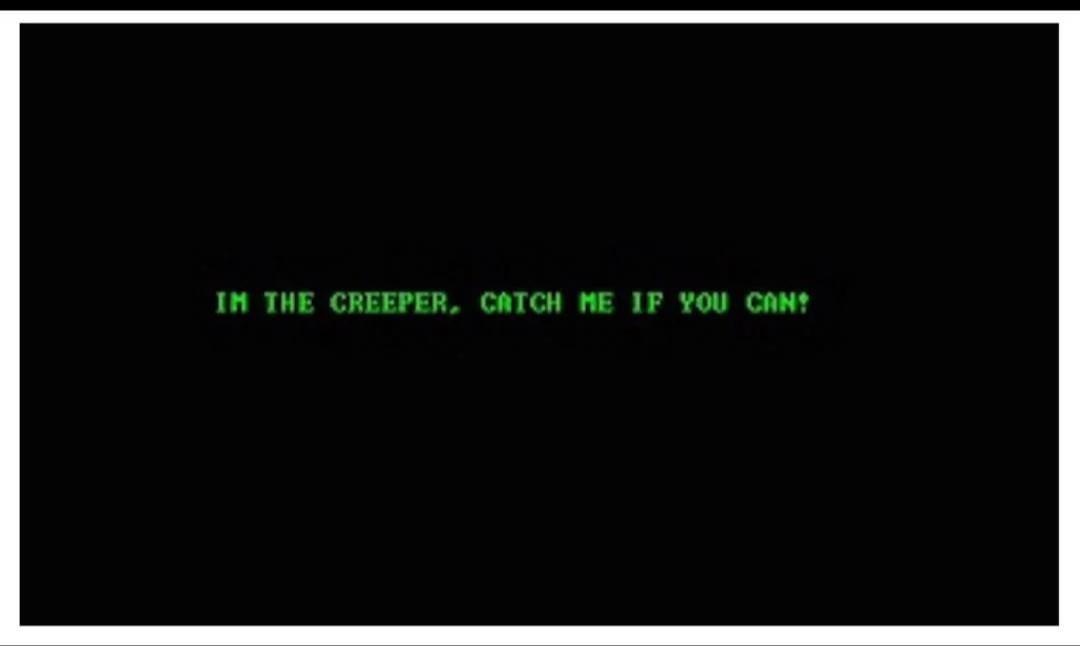
- Display a Message: Print the playful taunt: “I’m the creeper, catch me if you can!”
- Evade Overcrowding: Delete its previous instance to avoid overwhelming systems.
How Did Creeper Work?
- Propagation: Creeper transferred itself via the File Transfer Protocol (FTP) across connected DEC PDP-10 mainframes.
- Operating System: It relied on TENEX OS, which supported multitasking—core to its movement.
- Limitations: It could only jump to the next available system and didn’t embed deeply into systems or steal data.
The Birthplace: ARPANET and Its Role
Creeper’s existence was tied to ARPANET, a U.S. Department of Defense project linking universities and research labs. Key facts:
- Network Size: Only 15 sites in 1971, including MIT, UCLA, and Stanford.
- Intent: To test network survivability—making Creeper a “benevolent” stress test.
- Impact: Demonstrated vulnerabilities in distributed systems long before cybersecurity became an industry.
Legacy: From Harmless Experiment to Cybersecurity Catalyst
Though harmless, Creeper ignited pivotal developments:
1. The First Antivirus: Reaper
- Ray Tomlinson (inventor of email) created Reaper to hunt and delete Creeper instances. This made Reaper history’s first antivirus program.
2. Conceptual Groundwork
- Creeper proved self-replicating code was possible, influencing later research on worms (e.g., John Shoch’s 1978 experiments) and even inspiring tools like network diagnostics.
3. Ethical Frameworks
- Unlike modern worms (e.g., Stuxnet, Conficker), Creeper highlighted how self-replicating code could be used responsibly—a contrast to today’s destructive cyberattacks.
FAQs About the Creeper Program
Q: Was Creeper really the first computer virus?
A: Technically, it was a worm (spread via networks), not a virus (which attaches to files). Viruses emerged later in the 1980s.
Q: Did Bob Thomas intend to cause harm?
A: No. Creeper was an academic experiment with no data theft, corruption, or persistence.
Q: Why is Creeper important today?
A: It marks the start of cybersecurity awareness, underscoring the need for proactive defense in networked environments.
Conclusion: A Landmark in Digital History
Though primitive by today’s standards, the Creeper program represents a seminal moment in computing. It proved network-based self-replication was feasible while sparking ethical debates about technological boundaries. For cybersecurity professionals and tech historians, Creeper remains a reminder that innovation and responsibility must advance hand in hand—long before malware became a trillion-dollar threat.
Keyword Recap: First computer worm, ARPANET history, Bob Thomas Creeper, self-replicating program, TENEX OS, Reaper antivirus, early cybersecurity.
Optimize your knowledge of tech history—share this article to spread the story of the Creeper, the experiment that started it all! 🖥️🔒